
When you buy a hosting plan from Top.Host, you are basically “renting out” space on one of our servers. This server contains all of your website’s important data (passwords, customer information, content). The server is your website’s “home” and, like any other home, it must be secured for its owner to enjoy. Firewall Based Reputation System is here in order to take care of that!
Security is our priority so we have just created a new tool. In this blog post we will explain how it works, what it does and which are the tool’s advantages. We will also give you an insight on how malicious attacks work and how we protect you from them.
From Bitninja to Firewall Based Reputation System
Οur customers host their ideas, businesses and online presence οn our servers. You can imagine that the issue of server security is not new – it has been concerning us from day 1 of our operation. For many years, the hard task of our servers protection from malicious attacks was undertaken by the Bitninja cloud service. It is one of the most popular protection softwares and has largely covered our needs for several years.
However, as our clientele grew so did our needs. We needed more and we could not get it unless we went to a custom-made solution designed by ourselves. Creating our own tool, exactly tailored to fit our needs, was the only way! That’s how Firewall Based Reputation System arrived!
The new tool!
So our infrastructure team focused on this great task. Having the know-how and experience, the team designed and created its own Firewall Based Reputation System: it detects an IP as suspect by using the following methods:
- Brute Force attacks on
Email
FTP
Webmail
Plesk Control Panel - Website login forms (WordPress, Joomla, Drupal, PrestaShop and more)
- Attacks on websites with security gaps and not updated applications
- Attacks on forms such as contact/ subscription/ password reminder for Spam
This malicious IP is then blocked by the attacked server which forwards the information to the central Firerwall Based Reputation System. All Top.Host servers block the IP out so that it is no longer a threat.
This system ends up fortifying our customers against:
- DDOS attacks on Web service
- Spam
- CMS hacking (website infection)
- Spying on passwords through the email service and in the Plesk Control Panel
The following image shows an IP blocking graph per service.
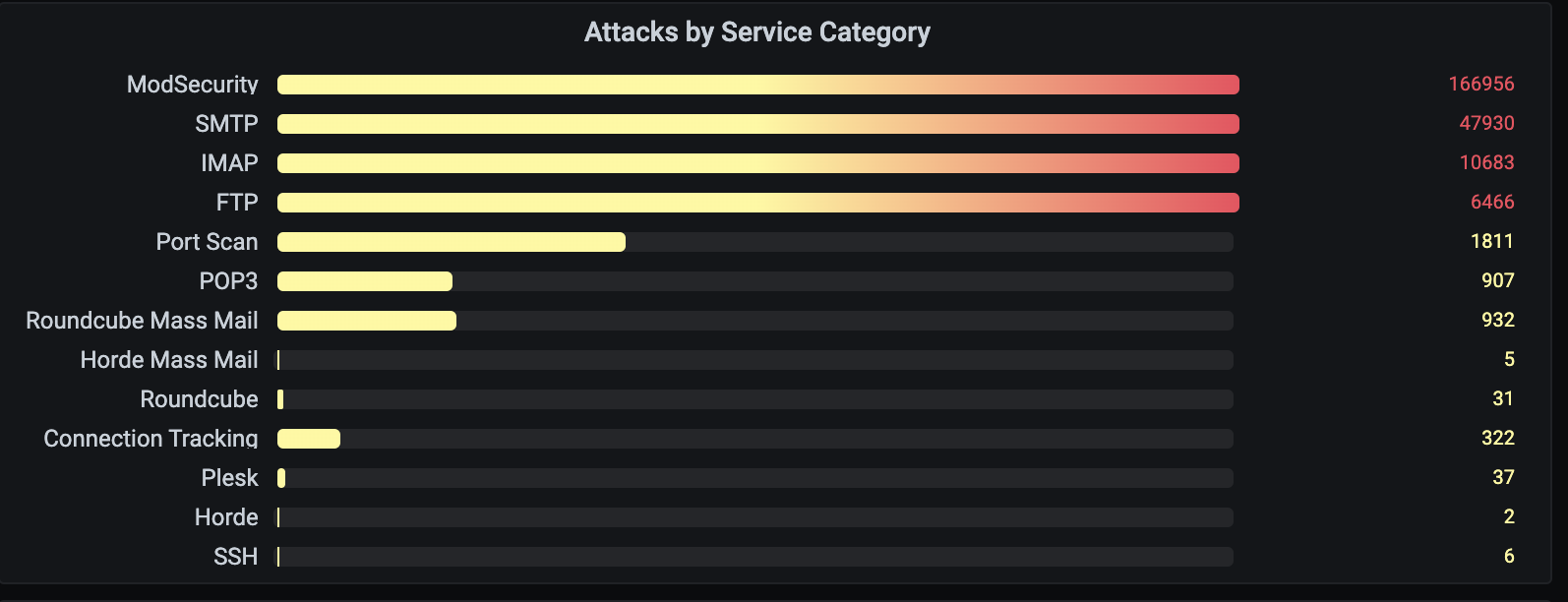
Top.Host customers are protected from day one thanks to this tool. There is no extra charge for that and there is no need to to anything in order to to activate this function. It is enabled by default on the servers provided by Top.Host!
Interesting facts gathered from the Firewall Based Reputation System
You can imagine that in order to create such a tool we had to invest time and resources. However, the attempted and stopped attacks are not few. Everyday there are way too many attacks attempted and motives behind them vary. But without a doubt they are also financial motives. The Firewall Based Reputation System has offered some impressive insights that highlight not only the importance of fortification but also the size of the problem.
Approximately 230,000 attacks a month
As you can see from the picture, the attempted attacks are thousands every day. Our tool manages to block them!
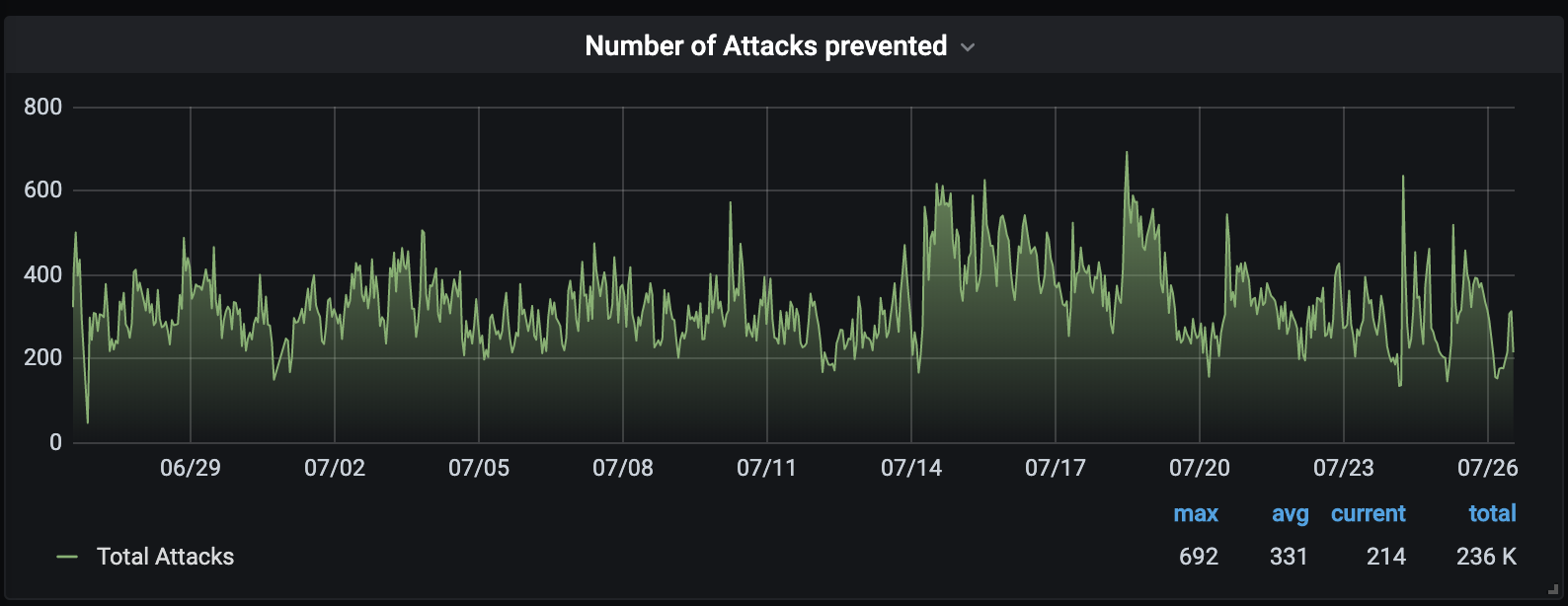
Monthly server breach attempts
Here is an example of attempted breaches on a single server, over a period of one month. It ‘s really impressive.
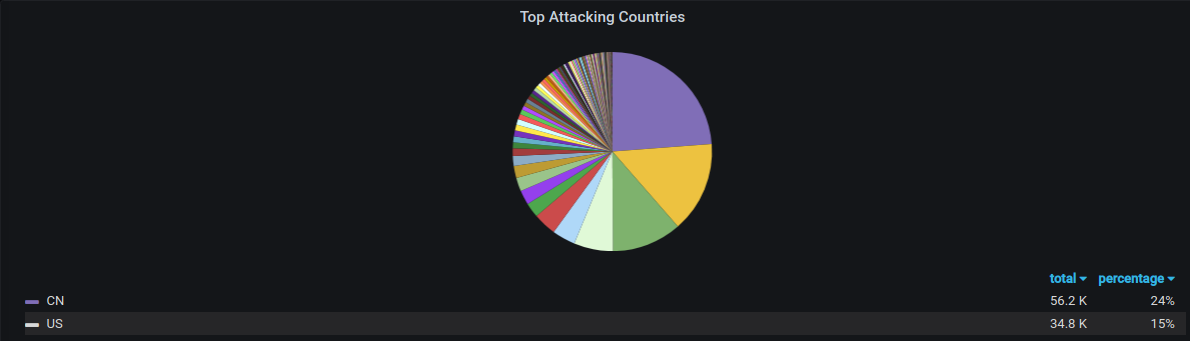
Geographical data
Most attempts are made from China and the United States!
Whatever the reason is for anyone on the planet to attack a server, we are here to prevent it. The new tool is just one part of our effort towards this direction!





Join the Discussion